Ceh Security Certification
The exam code for ceh certification version 10 is 312 50 and tests your capabilities in using penetration testing tools to evaluate computer systems and network security and.
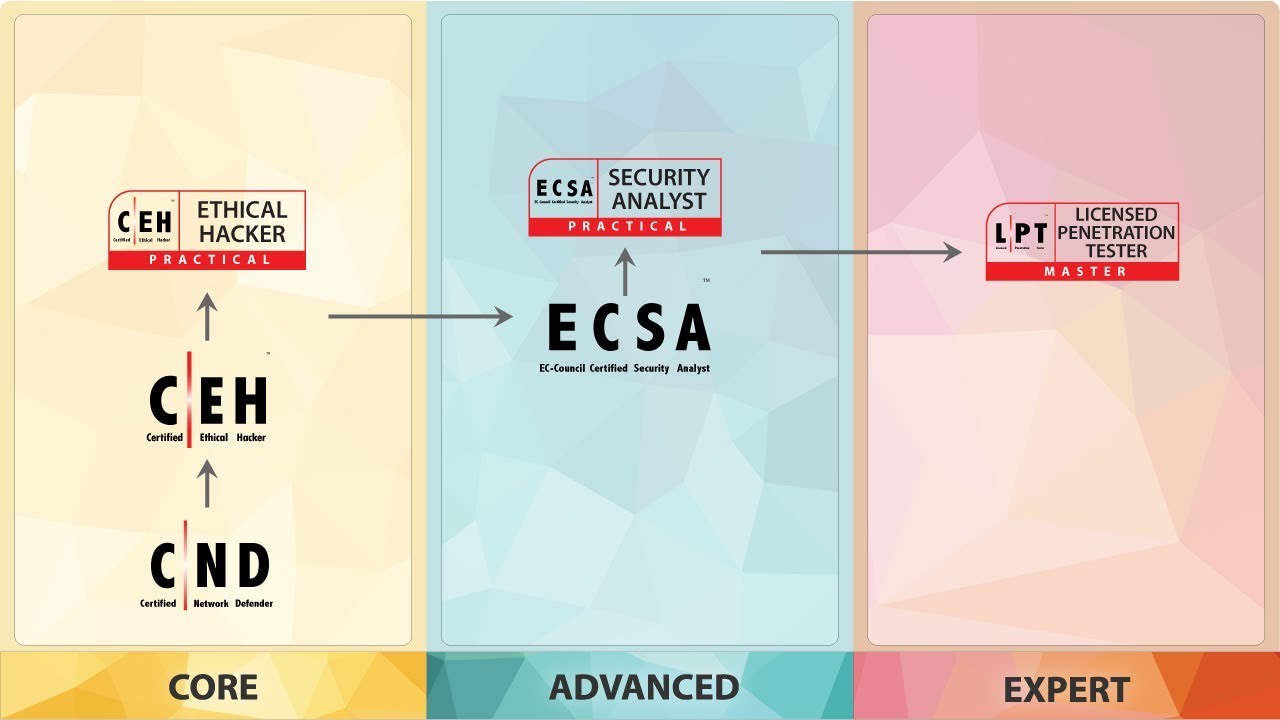
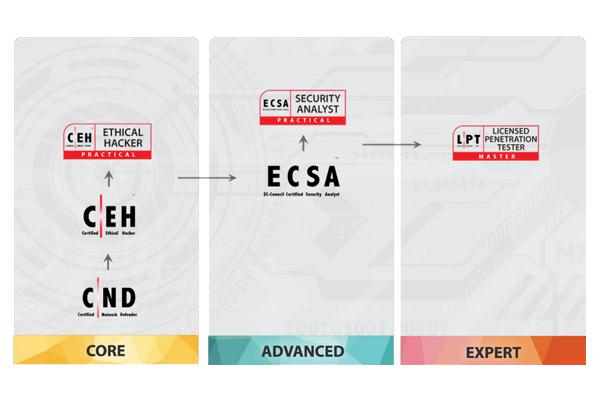
Ceh security certification. Youll learn the techniques and tools used by cybercriminals and how to apply them to conduct security assessments and report your findings. Cybersecurity training and certification programs that enable the information security workforce to create cisos ethical hackers cyber forensic investigators etc. The ceh is one of the foundational courses offered by ec council and it is a good starting point before venturing into the ec council certified security analyst esca exam. Information systems security professionals uses this certifications to show organizations that not only do they understand security concepts but can conduct an actual.
To become ceh certified you must pass the ceh examination after either attending ceh training at an accredited training center like simplilearn or through self study. The certified ethical hacker ceh certified network defense architect cnda by ec council are some of the most respected security certifications in the world. Information systems security professionals use this certification to show organizations that they understand security concepts and penetration testing. Ec council is a global leader in infosec cyber security certification programs like certified ethical hacker and computer hacking forensic investigator.
A recent addition to the ec council certification portfolio the ceh practical designation targets the application of ceh skills to real world security audit challenges and related scenarios. Candidates must attend official training or have at least two years of information security related experience. Certified ethical hacker ceh certification will enhance your ability to assess and analyze computer systems security to protect your corporate infrastructure. The certified ethical hacker ceh certification path teaches you the hacking skills necessary to successfully perform a penetration test.