Data Security Risk Assessment Template

A security risk assessment template is very important when you provide your private information to anyone or shift to a new place.
Data security risk assessment template. Download a security risk assessment template from here fill in the required details and print it out. Assess if an item is high medium low or no risk and assign actions for time sensitive issues found during assessments. Performing cybersecurity risk assessments is a key part of any organizations information security management program. 7500 security boulevard baltimore md 21244.
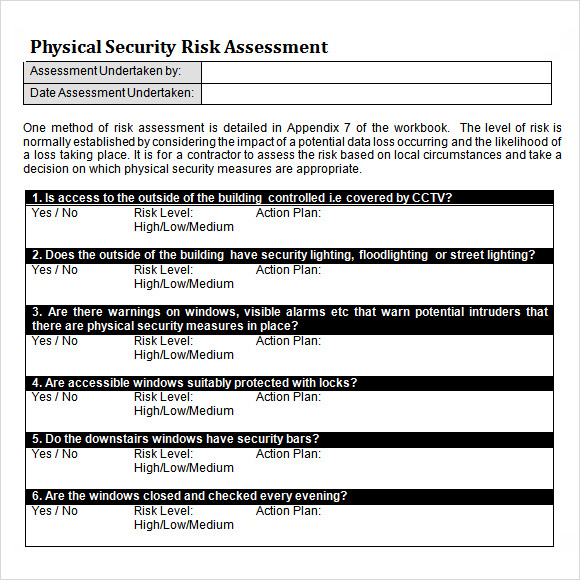
Everyone knows that theres some level of risk involved when it comes to a companys critical and secure data information assets and facilities. There might be some of your concerns that may not be included in the template. Physical security assessment template. An information security risk assessment template aims to help information security officers determine the current state of information security in the company.
Determine the information assets that you are aiming for. Information system risk assessment template docx home a federal government website managed and paid for by the us. Physical security assessment templates are an effective means of surveying key areas that may be vulnerable to threats. Nist sp 80039 managing information security risk risk analysis scope the scope of this risk assessment encompasses the potential risks and vulnerabilities to the confidentiality availability and integrity of all systems and data that acme creates receives maintains or transmits.
Its not uncommon to do a physical assessment before the start of a project on a site to determine the best layout that will maximize strength. Create a threat modeling exercise as this will let you and your. As detailed in the it risk assessment template develop and deploy appropriate questionnaires to obtain and document all possible information about the systems including physical infrastructure and topology people and processes security and backup policies criticalities sensitivities. Locate them and then begin security check.
But if youre just looking for the simple steps such as one might find in an assessment template word then we have them here.