Information Security Policy Template Free

A security policy template enables safeguarding information belonging to the organization by forming security policies.
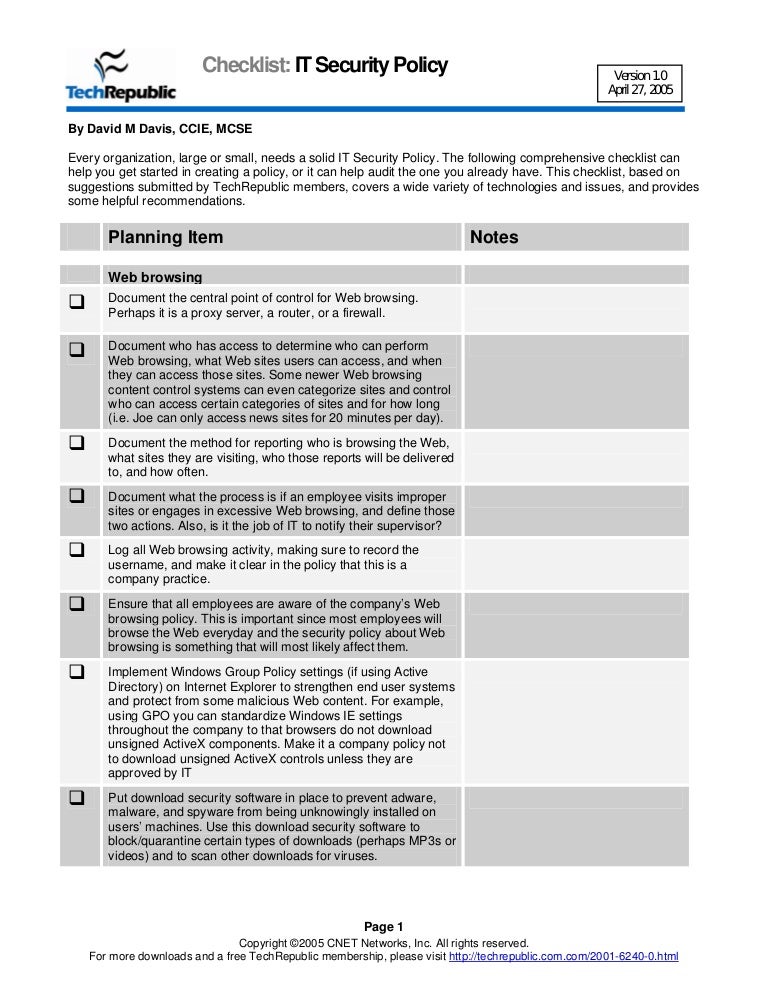
Information security policy template free. Youll find a great set of resources posted here already including policy templates for thirteen important security requirements. This will allow you to concentrate on developing the robust protection. A policy is typically a document that outlines specific requirements or rules that must be met. The list includes just about any kind of infosec document you can think of from remote access policies to information.
It may be necessary to make other adjustments as necessary based. Help with creating an information security policy template. However you manage your customers it is essential that you have a robust well thought out information protection policy in place. Once completed it is important that it is distributed to all staff members and enforced as stated.
The information security policy is one of the most important documents in your isms. So you need to write an information security policy. Types of security policy templates. Knowing where to start when compiling your information security policy can be difficult especially in large or complex organisations where there may be many objectives and requirements to meet.
Feel free to use or adapt them for your own organization but not for re publication or. The ultimate goal of the list is to offer everything you need for rapid development and implementation of information security policies. The sample security policies templates and tools provided here were contributed by the security community. Information security policy templates.
Free information security policy templates courtesy of the sans institute michele d. In the informationnetwork security realm policies are usually point specific covering a single area. 13 fantastic resources for writing an information security policy. Guel and other information security leaders.
A security policy enables the protection of information which belongs to the company. For example an acceptable use policy would cover the rules and regulations for appropriate use of the computing facilities. These include improper sharing and transferring of data. The information security policy template that has been provided requires some areas to be filled in to ensure the policy is complete.
Subscribe to sans newsletters. These issues could come from various factors. No matter what the nature of your company is different security issues may arise. Two days left to get an ipad 32g galaxy tab a or 250 off online training.