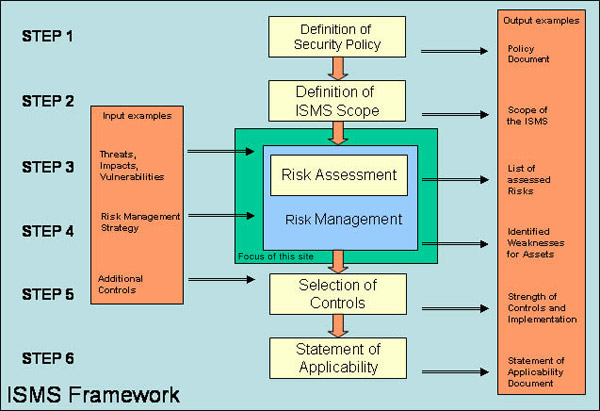
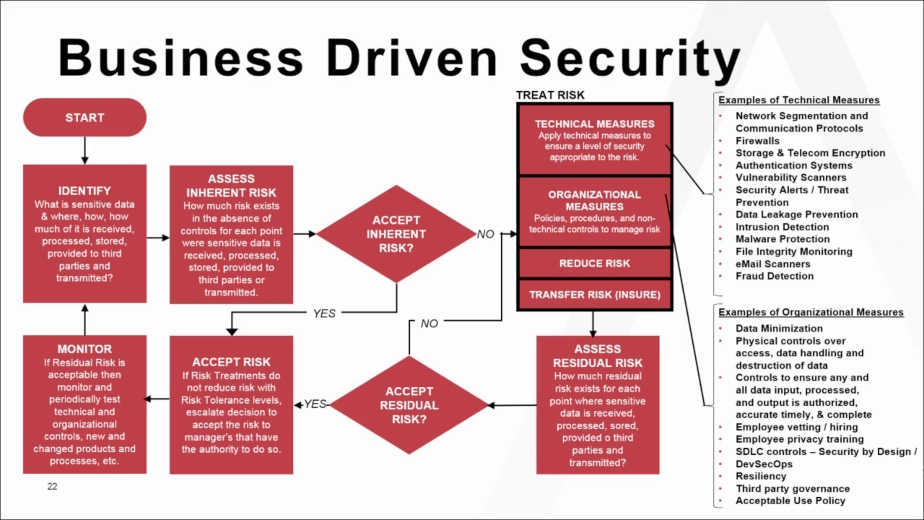
Information Security Risk Management Policy Template

The irm policy should be a subset of the organizations overall risk management policy risks to a company include more than just information security issues and should be mapped to the organizational security policies which lay out the acceptable risk and the role of security as a whole in the organization.
Information security risk management policy template. To support your risk management planning this page offers multiple templates that are free to download. To accomplish this task a formal information security risk management program has been established as a component of the universitys information security program as defined in the charter to ensure that the university is operating with an acceptable level of risk. Developed by experts with backgrounds in cybersecurity it risk assessment each template is easy to understand. It doesnt have to necessarily be information as well.
There are however no quick fixes. Prior to creating or reevaluating an it risk management policy an organization should weigh identified risks and analyze changes in existing policies laws and regulations involving information technology. A risk management policy should be in support of the organizations mission and deliverable and should be ratified by executive management and based on high priority. Feel free to use or adapt them for your own organization but not for re publication or for profit use.
The risk management policy statements should place a very high priority on managing organizational risk both strategically and systematically. Personalizing your cybersecurity it risk assessment template requires careful thought and planning by your organizations security risk management and executive leaders. The information security risk management program includes the process for managing exceptions to the information security policy and the risk acceptance process. Risk management is the process of identifying risks analyzing them to assess their likelihood and potential impact on a program and developing and implementing methods for responding to each risk.
The information security risk management program is described in this policy. Conducting a security risk assessment even one based on a free assessment template is a vital process for any business looking to safeguard valuable information. Risk management process flow. It could be an item like an artifact or a personwhether its for physical.
In simple terms risk management is about validating that protective measures are operational and appropriate to protect an organizations assets.