Logical Access Control Policy Template
23 access control methods access to data is variously and appropriately controlled according to the data classification levels described in the information security policy.
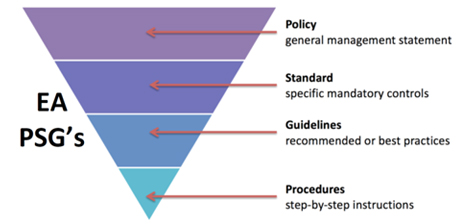
Logical access control policy template. Physical protection policy sample required written policy 10 purpose. This policy addresses all system access whether accomplished locally remotely wirelessly or through other means. Scope the scope of this policy is applicable to all information technology it resources owned or operated by organization name. The access control program helps organization name implement security best practices with regard to logical security account management and remote access.
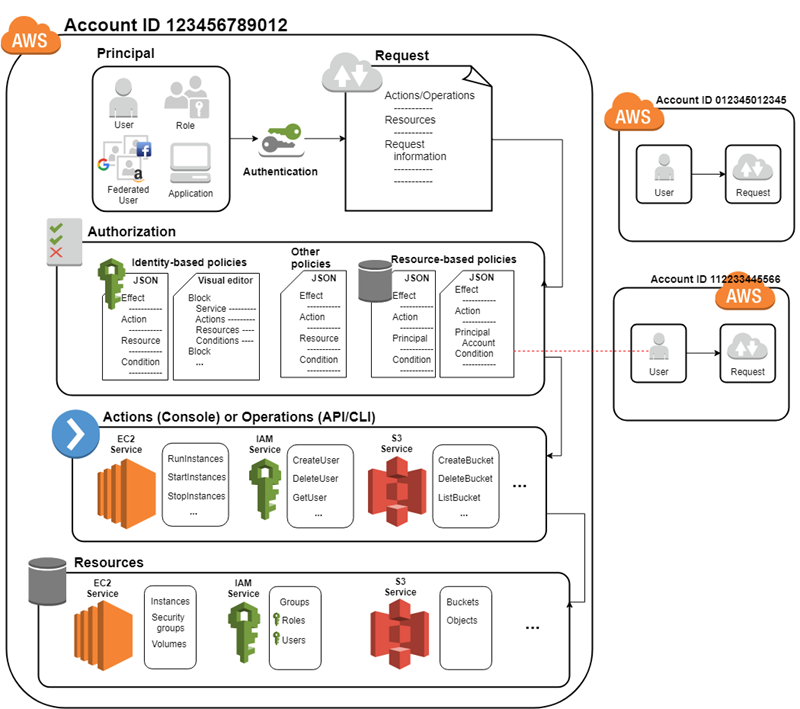
Represents the nist specified identifier for the access control family. The following subsections in this document outline the access control requirements that the state and each agency must develop or adhere to in order to be compliant with this policy and to ensure that logical and physical access to. This logical access control policy applies to all information systems applications and data housed within or supported by the university and to all individuals who have access to those systems applications or data including employees permanent temporary. Access control is the process that limits and controls access to resources of a computer system.
Access control policies eg identity based policies role based policies attribute based policies and access enforcement mechanisms eg access control lists access control matrices cryptography are employed by organizations to control access between users. All physical logical and electronic access must be. It access control and user access management policy page 2 of 6 5. This policy is intended to meet the control requirements outlined in sec501 section 81 access control family controls ac 1 through ac 16 ac22 to include specific requirements for vita in ac 2 cov and ac 8 cov.
Nearly all applications that deal with financial privacy safety or defense include some form of access authorization control. P1 the information system enforces approved authorizations for logical access to the system in accordance with applicable policy. Prior card has been cancelled. Users are students employees consultants contractors agents and authorized users.
Adequate security of information and information systems is a fundamental management responsibility. Access control is concerned with determining the allowed activities of legitimate users mediating every attempt by a user to access a resource in the system. New cards with the same level of access control will be issued through the library.