Nist Risk Acceptance Template
Lipner and butler w.
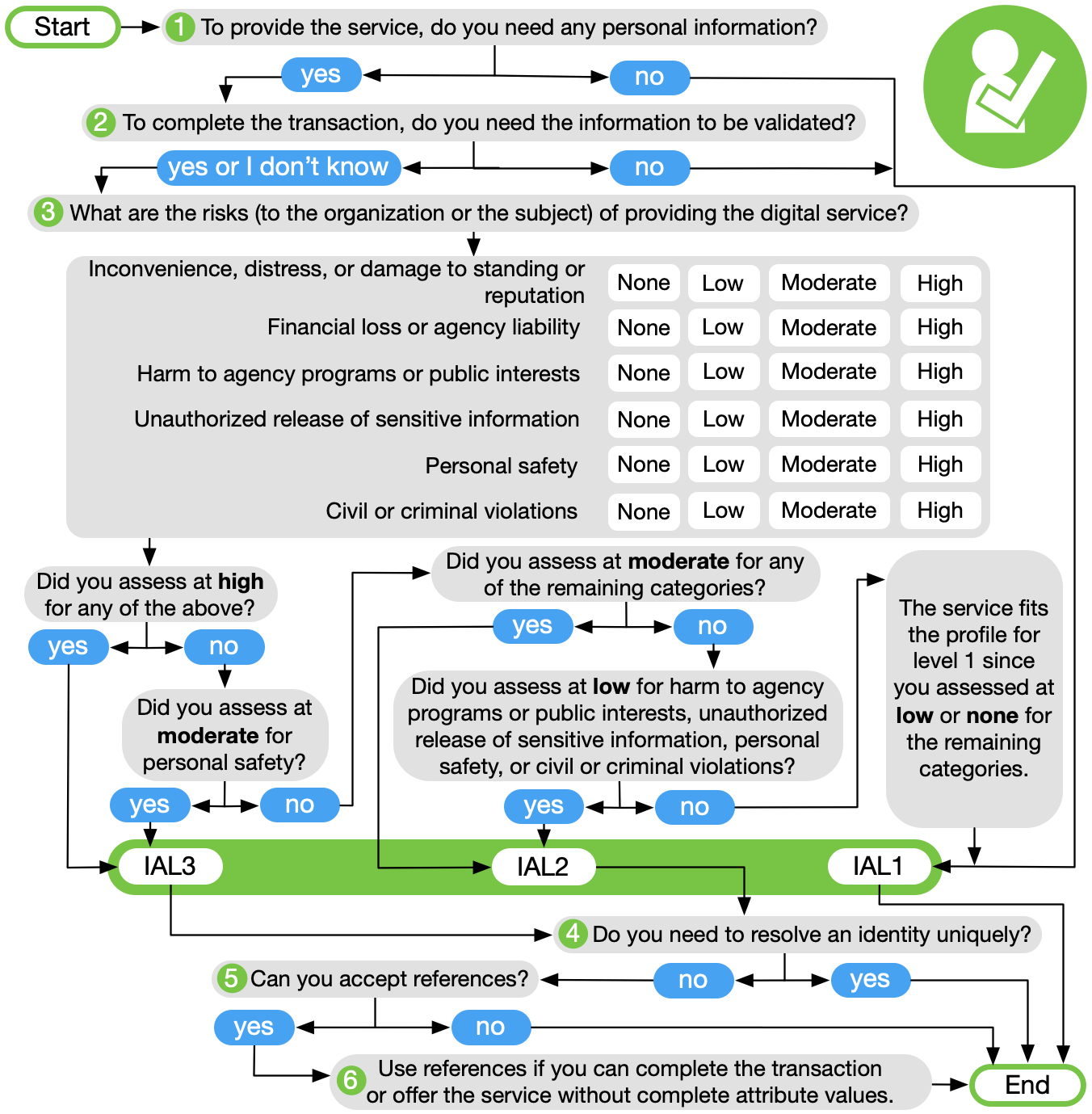
Nist risk acceptance template. Costly explain to mitigate risk. Information security will also provide a strong basis for reciprocal acceptance of security authorization decisions and facilitate information sharing. Instructions for risk acceptance form. Risk management and the cybersecurity of the us.
The secretary of commerce shall on the basis of standards and guidelines developed by nist prescribe standards and guidelines pertaining to. That signature should not however hold the ciso accountable for the business choice that is made. It is the basis of the nist framework for improving critical infrastructure cybersecurity. Lampson executive summary risk management is a fundamental principle of cybersecurity.
Nist 800 171 policy and procedures template is a bundle of templates that help implement the nist sp 800 171 system security requirements. Risk acceptance at the executive level by jack jones. The systems business owner is responsible for writing the justification and the compensating control or remediation plan. Special publication 800 39 managing information security risk organization mission and information system view compliance with nist standards and guidelines.
In accordance with the provisions of fisma 1. The cisos signature on the risk acceptance form should hold himher accountable for providing accurate and meaningful information to the decision makers. This form is to be used to justify and validate a formal risk acceptance of a known deficiency. The systems business owner is responsible for writing the justification and the compensating control or remediation plan.
The quick start guides build on the nist standards and guidance consolidate information from various nist publications and provide sample ways to implement the standards and. Please complete all risk acceptance forms under the risk acceptance rbd tab in the navigation menu. Government input to the commission on enhancing national cybersecurity steven b. Instructions for risk acceptance form this form is to be used to justify and validate a formal risk acceptance of a known deficiency.
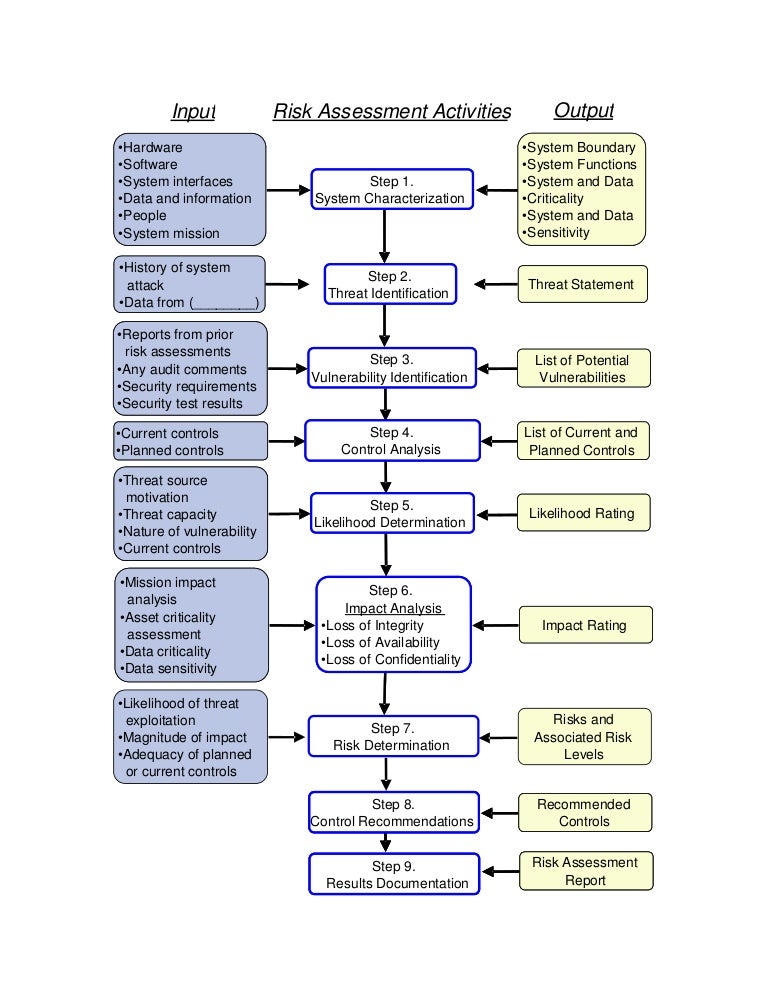
Nist jtf leader johns hopkins apl the mitre corporation nist. Guide for conducting risk assessments. The risk management framework rmf provides a structured yet flexible approach for managing the portion of risk resulting from the incorporation of systems into the mission and business processes of the organization. Nist control deficiency or vulnerability andor other identified risk factor.
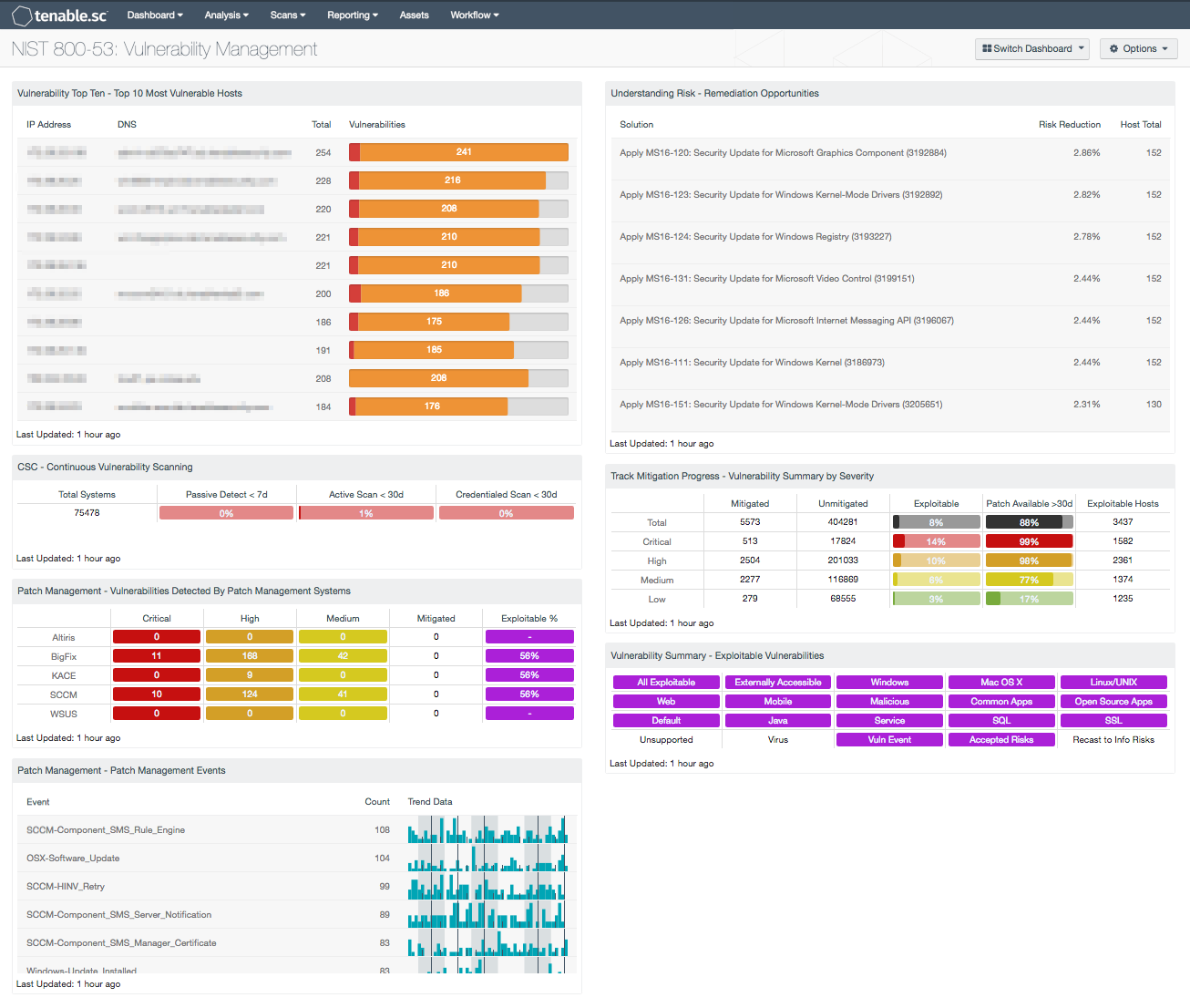
Agency signatures s igning below is the acknowledgement and acceptance of the risk outlined in the initial section of this document. Cfacts can be accessed at httpscfacts3cmscmsnet. Cms information security policystandard risk acceptance template of the rmh chapter 14 risk assessment. It is a requirement that a compensating control or remediation plan be defined.