Vulnerability Management Certifications

Comprehensive reconnaissance enumeration and discovery techniques are the prime elements of successful vulnerability assessment.
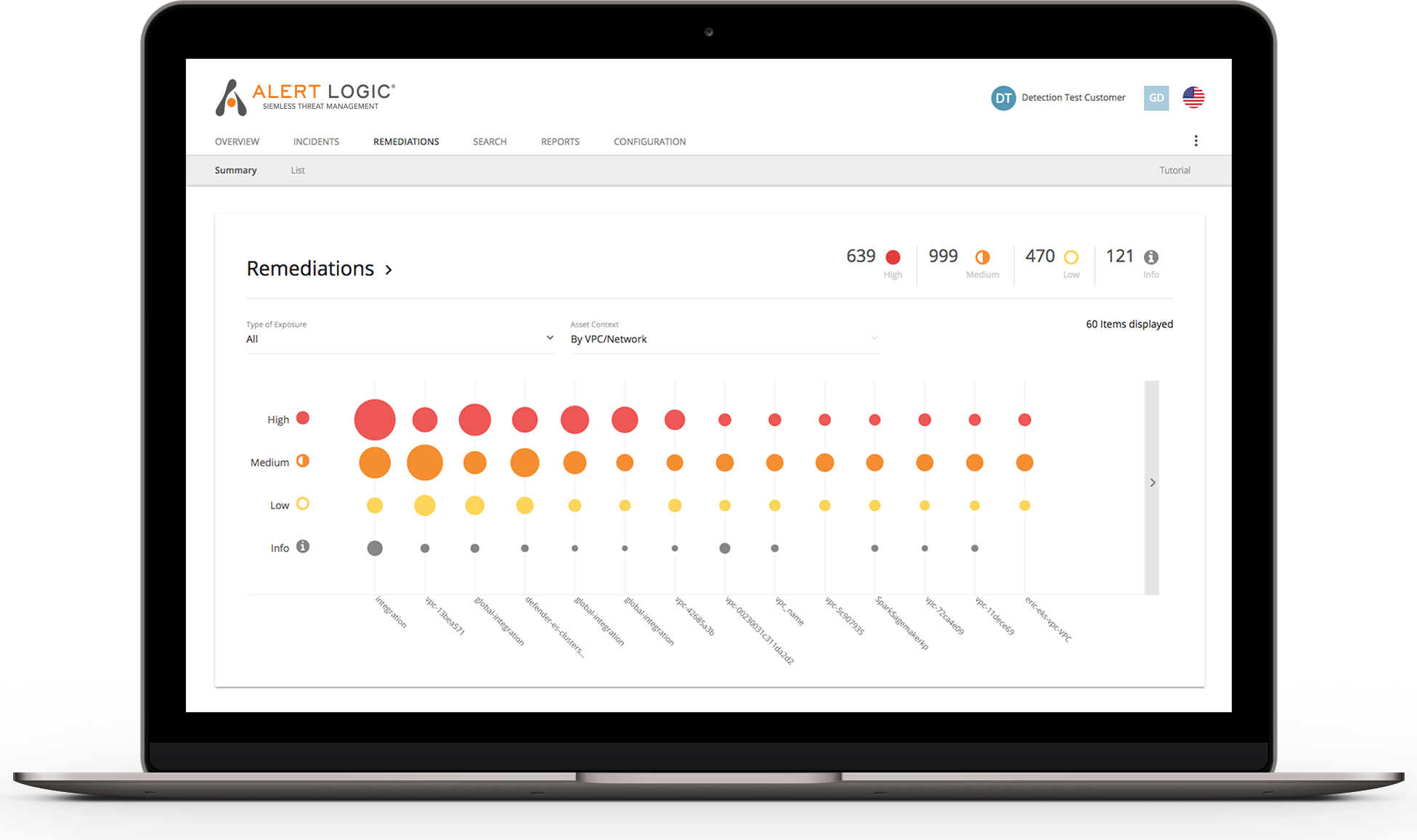
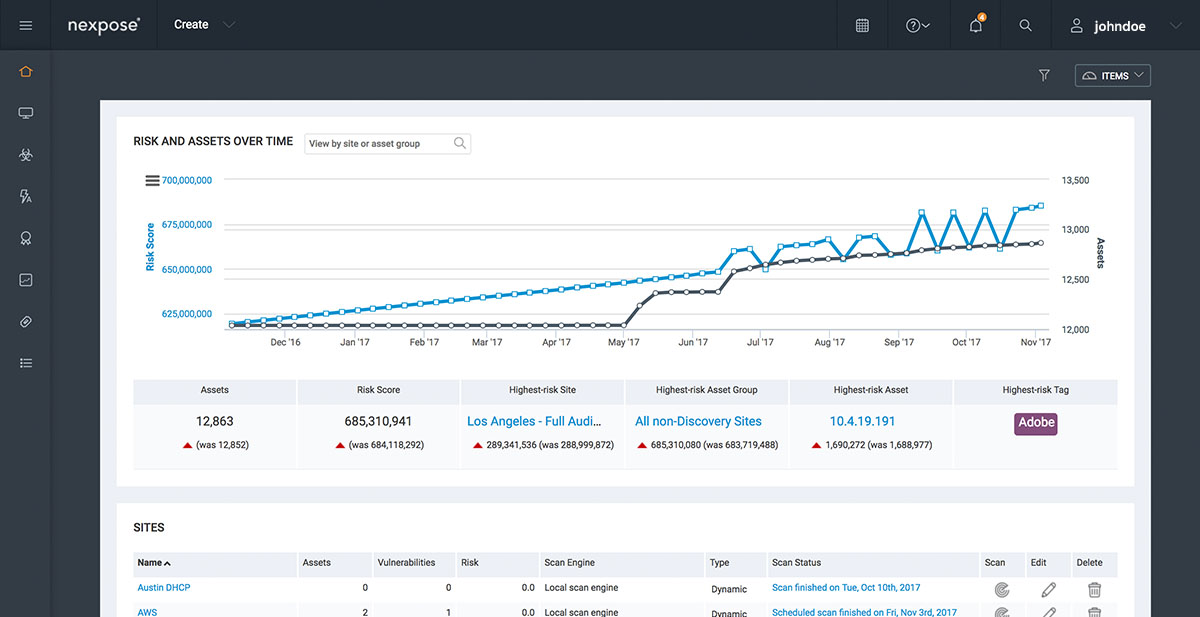
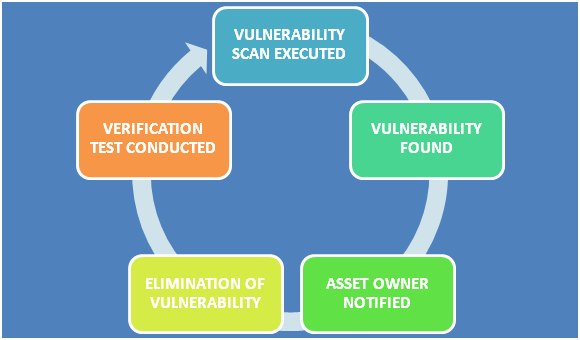
Vulnerability management certifications. Mile2 has a specific vulnerability assessment certification cva but cissp and penetration testing certs are often cited as must haves. Some useful information to keep in mind. Vulnerability assessment and management. The objective for vulnerability management analysts is to determine internal and external weaknesses report and resolve them.
This micro certification covers usage of popular scanning tools delivery of progress reports and implementation of increased system coverage. Exam is 2 hours in length. Although somewhat similar to penetration testing. Assetview and threat protection increase visibility on your assets and understand threats to your organization.
Vulnerability management is a continuous information security risk process that requires the oversight of management. The cissp certification is a globally recognized standard of achievement that confirms an individuals knowledge in the field of information security. Certifications for vulnerability assessors weve listed a variety of certifications that crop up in job descriptions. Certifications addressing security and risk management asset security.
Prior experience in information assurance incident handling vulnerability management and vulnerability analysis and assistance programs. Exam purchase is good for one 1 exam attempt. Vulnerability management get started with the basics of vulnerability management. Once the exam begins students may not pause or stop the exam.
Certifications are taken online at the students convenience and are an open book format. Having mastered the structural foundations of vulnerability management the second module of sec460 will pivot to the realm of direct tactical application. Advanced scanning scan a complex networks of devices. Graduate certificates in computer forensics and vulnerability managementdesigned for individuals with the necessary background in networking programming and operating systems the computer forensics and vulnerability management certificates provide students with essential skills for managing investigating monitoring and protecting against cyber attacks.
Cissps are information assurance professionals who define the architecture design management andor controls that assure the security of business environments.