Vulnerability Management Template

While the methodology can be implemented in different domains and the organization as a whole it is mostly related to network security.
Vulnerability management template. This template will allow you to create a vulnerability management policy. Scope of the program. Some of the more recent data breaches include that of the equifax data breach and the breach from the friend finder network. Policy changes or exceptions are governed by the.
Compliance compliance shall be evidenced by implementing vulnerability management procedure as described above. Members of the vulnerability management team. By creating a patch and vulnerability management plan organizations can help ensure that it systems are not compromised. O credentialed scan of host with vulnerability scanner that is capable of detecting known vulnerabilities o perform annual vulnerability scanning.
This vulnerability management process template provides a basic outline for creating your own comprehensive plan. However this document also contains information useful to system administrators and operations personnel who are responsible for applying. Vulnerability management is a key component in planning for and determining the appropriate implementation of controls and the management of risk. Vulnerability management vm is the means of detecting removing and controlling the inherent risk of vulnerabilities.
Documenting procedures for patch management is a vital part of ensuring cybersecurity. The topics of the other crr domains provide information about vulnerable conditions asset. Vulnerability management solution remediation service levels the primary vulnerability assessment solution is retina cs enterprise vulnerability management from beyondtrust. Formal vulnerability assessment template.
This is separate from your patch management policy instead this policy accounts for the entire process around managing vulnerabilities. Vulnerability management is a stepwise process that deals with the identification and mitigation of vulnerabilities. A breach is a successful attack on the system. Scanning schedule for vulnerability scanning.
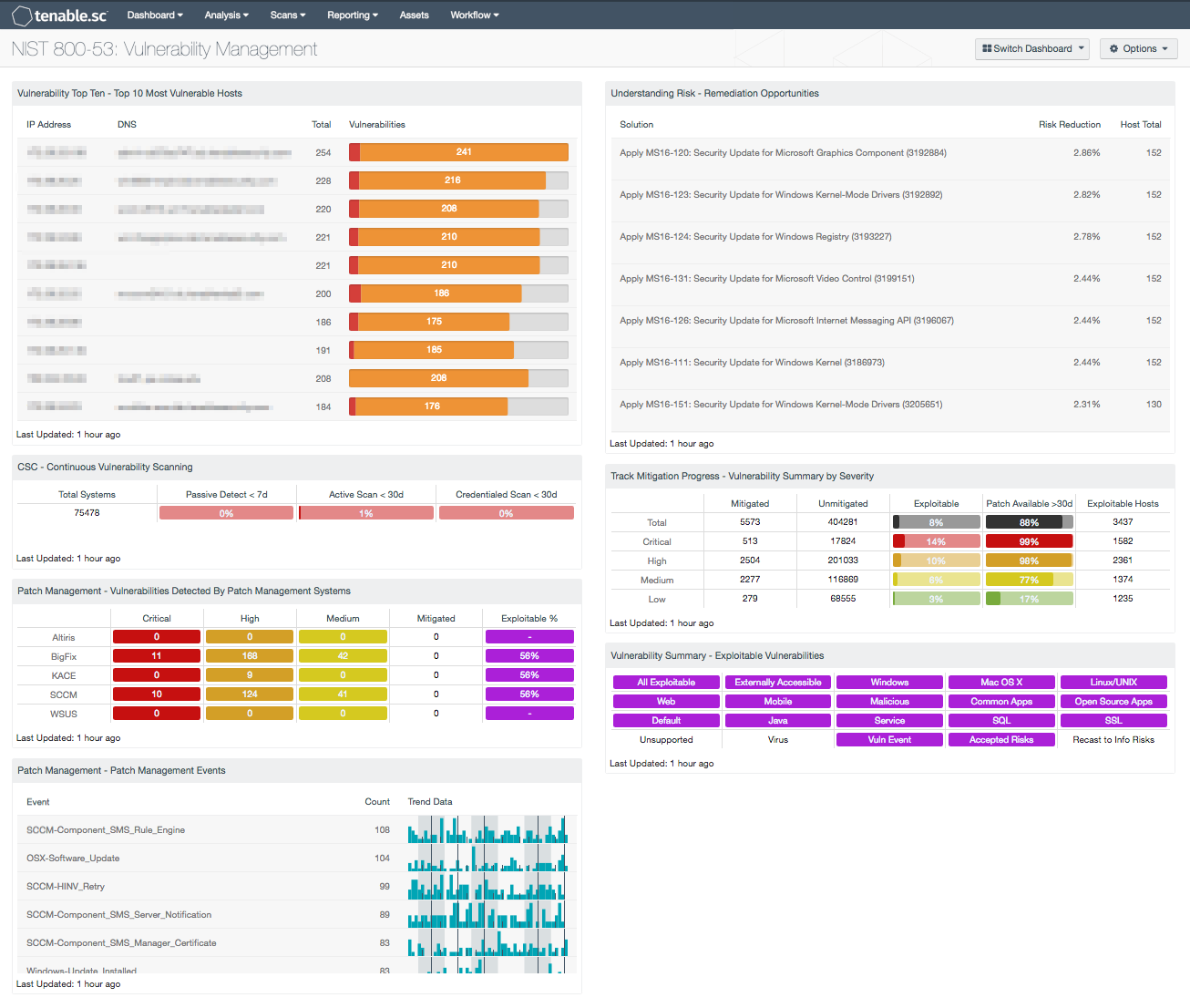
Retina scans the network infrastructure for devices on a scheduled periodic basis and generates a report on the vulnerabilities identified across all assets. It is reasonable to say that vulnerability management is central to cyber resilience. The vulnerability management program utilizes specialized software and workflow to help eliminate detected risks vulnerability management for d ummies 2008. This document provides guidance on creating a security patch and vulnerability management program and testing the effectiveness of that program.
Cost savings estimate vulnerability patch management program vpmp when you look at the costs associated with either 1 hiring an external consultant to write cybersecurity documentation for you or 2 tasking your internal staff to write it the cost comparisons paint a clear picture that buying from complianceforge is the logical option.