Pki Certificate Authority

On the setup type page verify that enterprise ca is selected and then click next.
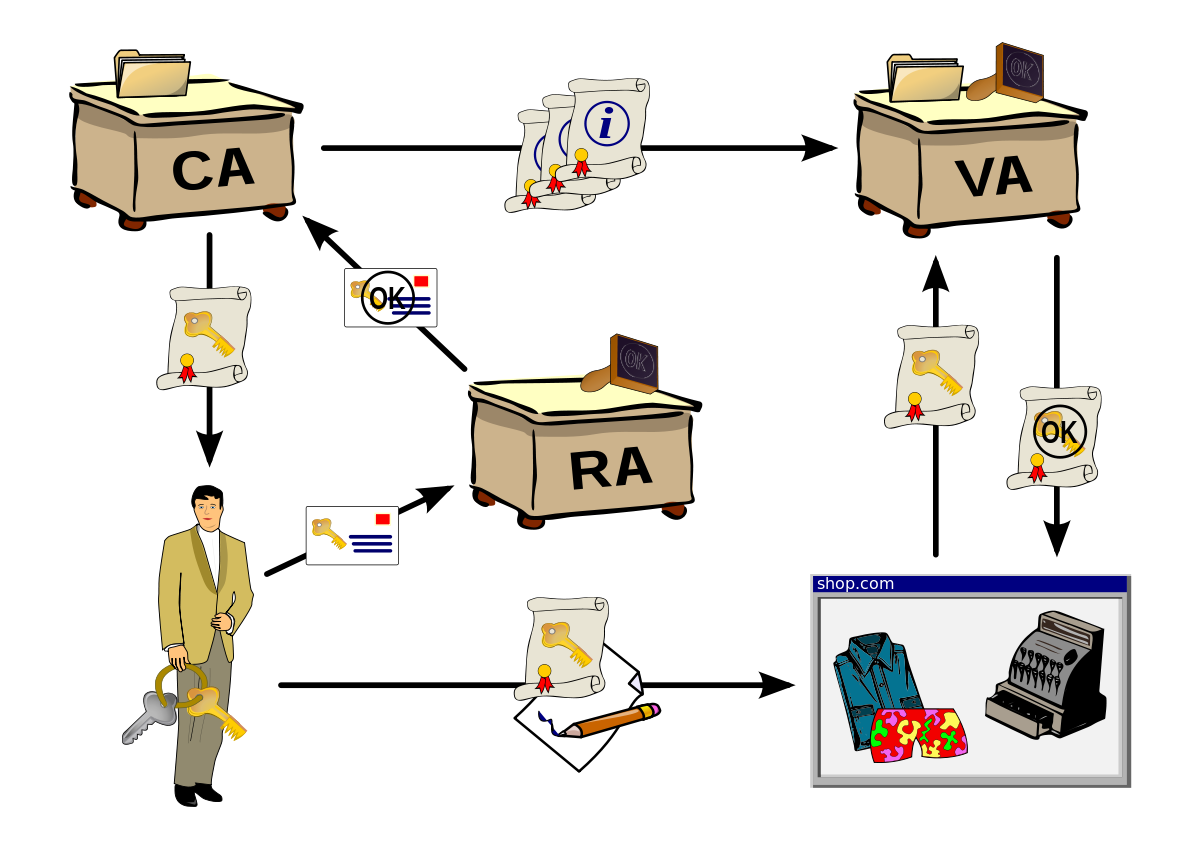
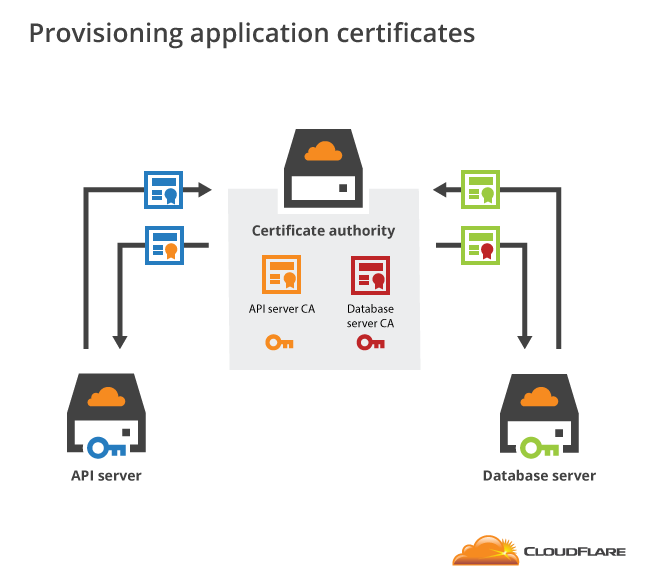
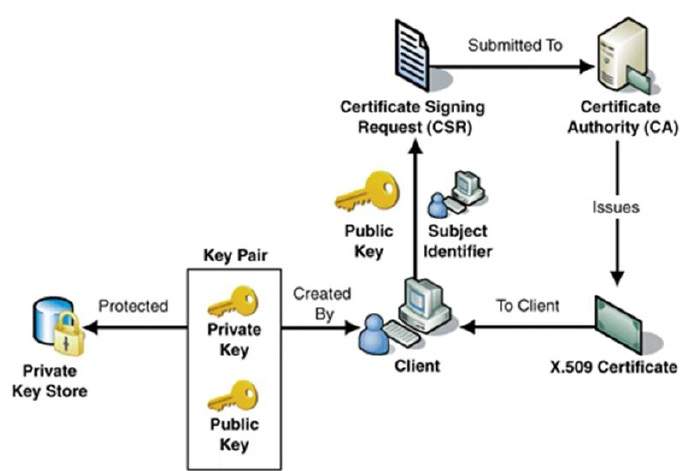
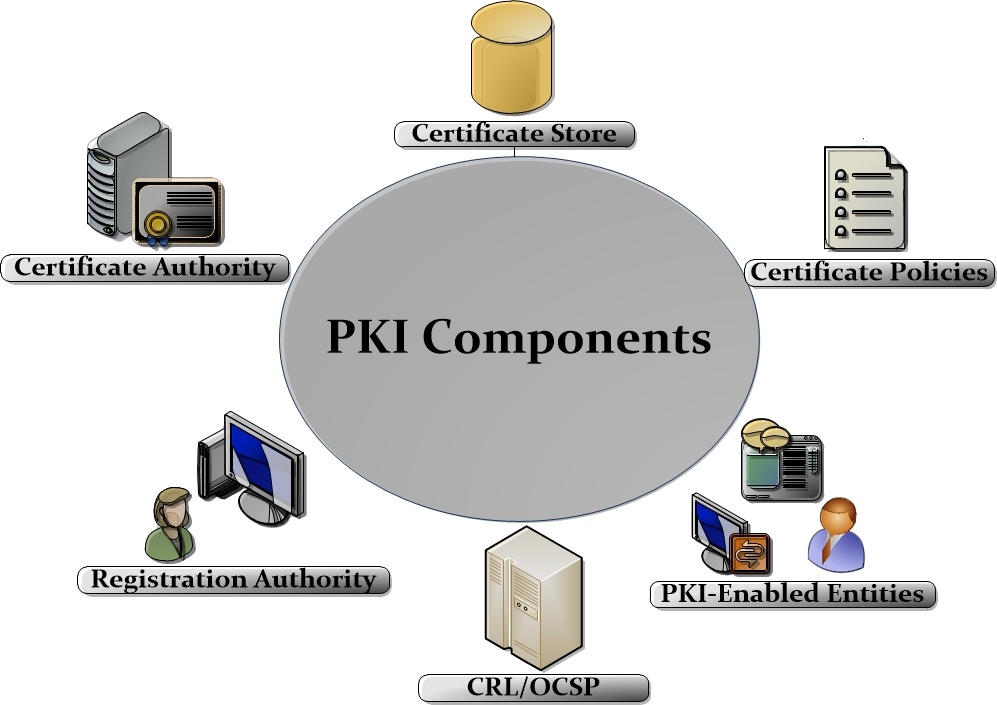
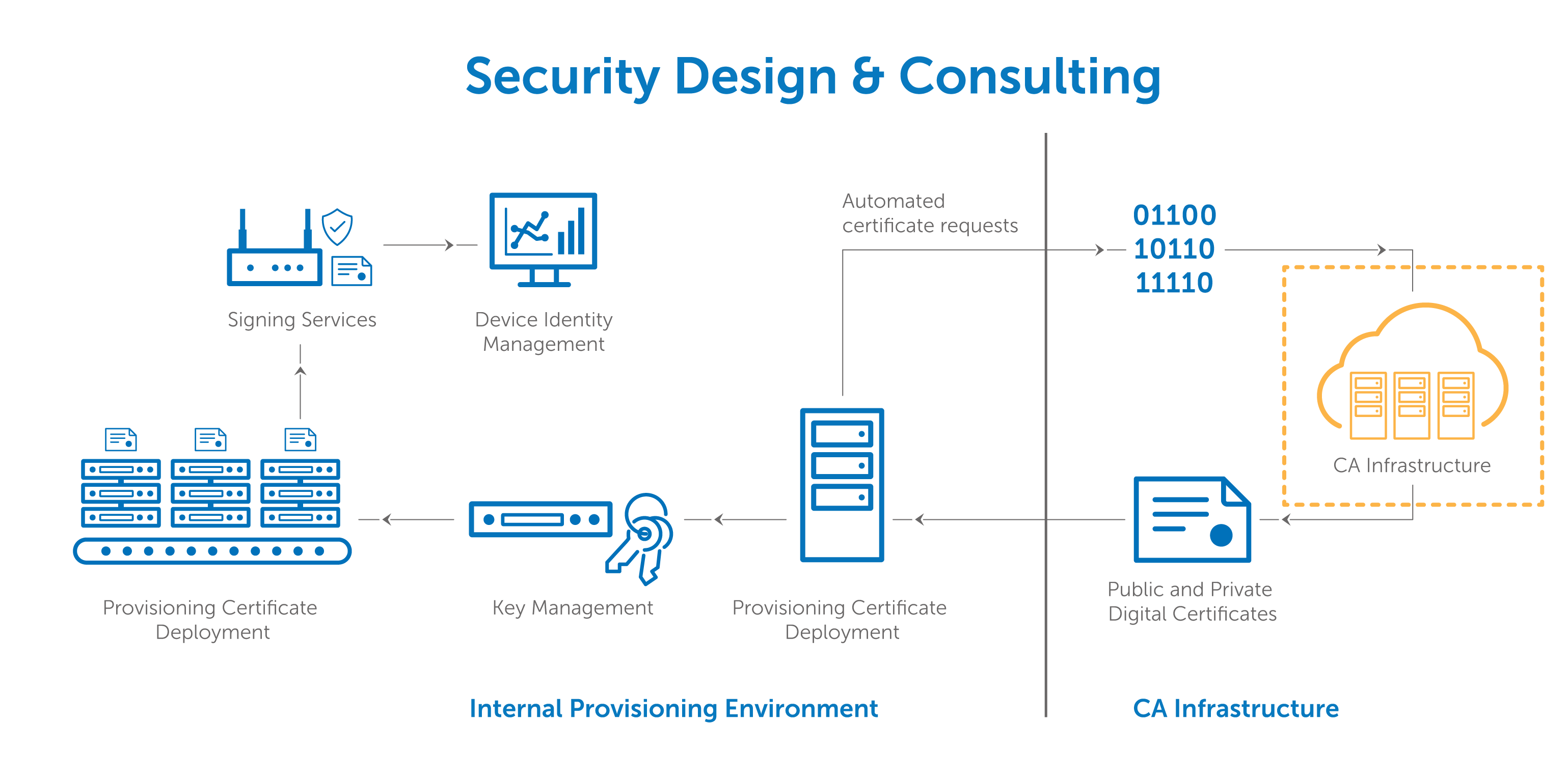
Pki certificate authority. External certification authority eca pki the dod has established the external certification authority eca program to support the issuance of dod approved certificates to industry partners and other external entities and organizations who do not otherwise have access to dod approved pki credentials. Public key infrastructure design guidance before you configure a public key infrastructure pki and certification authority ca hierarchy you should be aware of your organizations security policy and certificate practice statement cps. A certification authority to issue certificates a trusted ca is the only entity that can issue trusted digital certificates. On the specify the type of the ca page verify that root ca is selected and then click next.
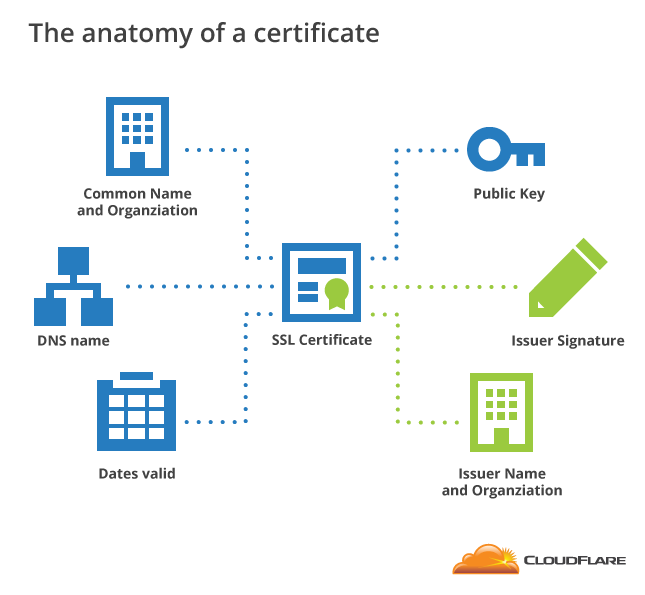
These digital certificates are based on cryptography and follow the x509 standards defined for information security. In a microsoft pki a registration authority is usually called a subordinate ca. Certification authority backup falls under a pki recovery plan. By managing the full lifecycles of digital certificate based identities entrust authority pki enables encryption digital signature and certificate authentication capabilities to be consistently and transparently applied across a broad range of applications and platforms.
This is extremely important because while pki manages more of the encryption side of these certificates authentication is vital to understanding which entities own what keys. An ra is responsible for accepting requests for digital certificates and authenticating the entity making the request. Make sure you have a full documentation about your public key infrastructure deployment. The pki role that assures valid and correct registration is called a registration authority ra.
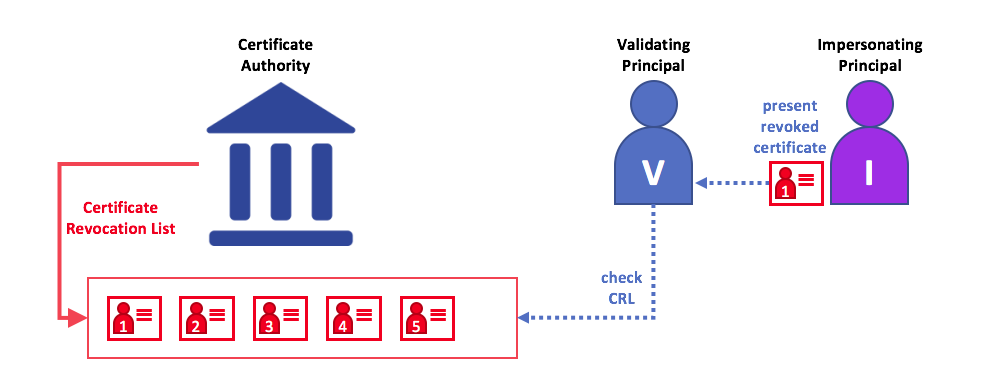
The federal pki fpki is a network of certification authorities cas that are either root intermediate or issuing cas. Using at least one subordinate ca can help protect the root ca from unnecessary exposure. Most likely you would have most of your documentation during the design a pki hierarchy phase.