Network Security Plan Template
This template is part of a comprehensive it governance and compliance toolkit.
Network security plan template. Templates makes the planning easy for you while you need not keep all points of security in your head and get inspired by the template format to frame it all. System administrators also implement the requirements of this and other information systems security policies standards guidelines and procedures. In the informationnetwork security realm policies are usually point specific covering a single area. It can be branded to your organization.
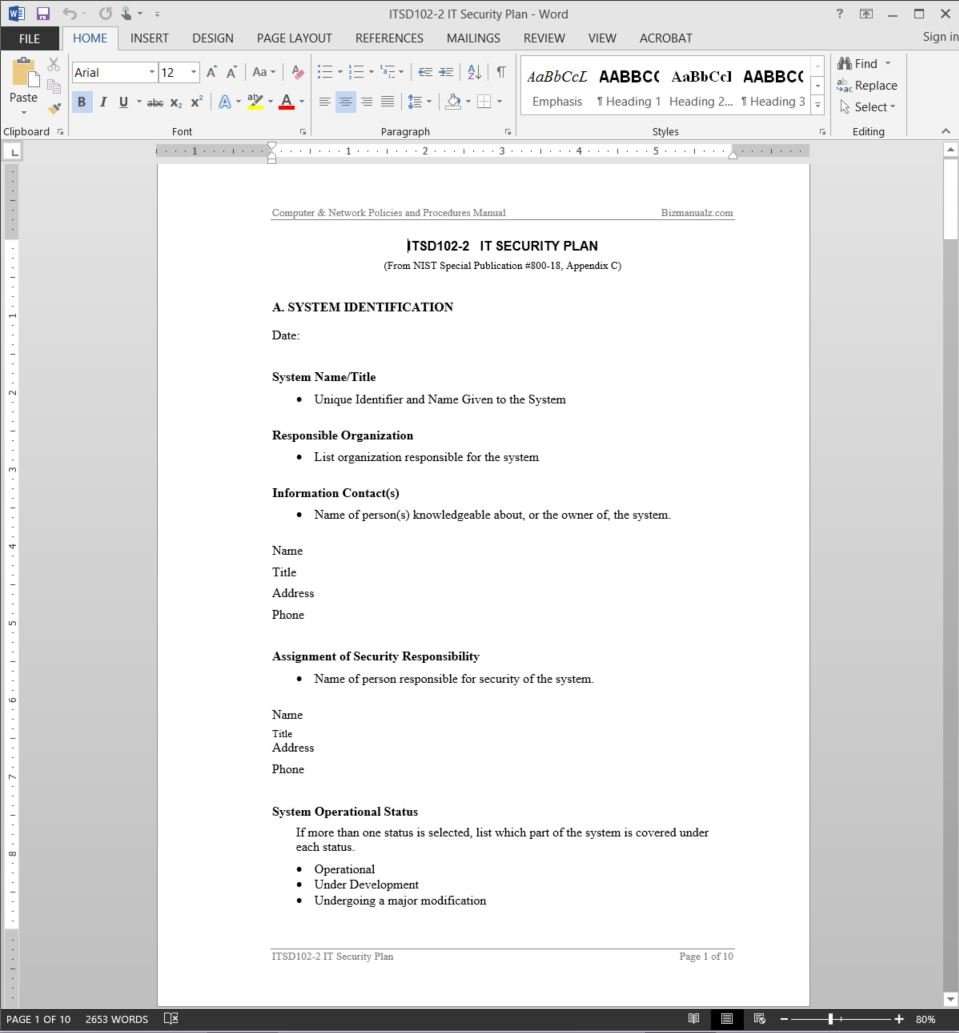
Security plan template ms wordexcel use this security plan template to describe the systems security requirements controls and roles responsibilities of authorized individuals. Pl 2 system security plan security control requirement. This toolkit is a collection of microsoft word forms templates and instructional documents that help you assess and establish the crucial policies that you need to operate a secure and compliant it organization. For example an acceptable use policy would cover the rules and regulations for appropriate use of the computing facilities.
Key contact information for service providers such as third party network administrators security monitoring phone internet etc. These individual documents can be inserted into the plan document diretly or attached as appendices. This network security policy template provided by toolkit cafe provides companies with guidance for implementing network security to ensure the appropriate protection of corporate networks. Network security related activities to the security manager.
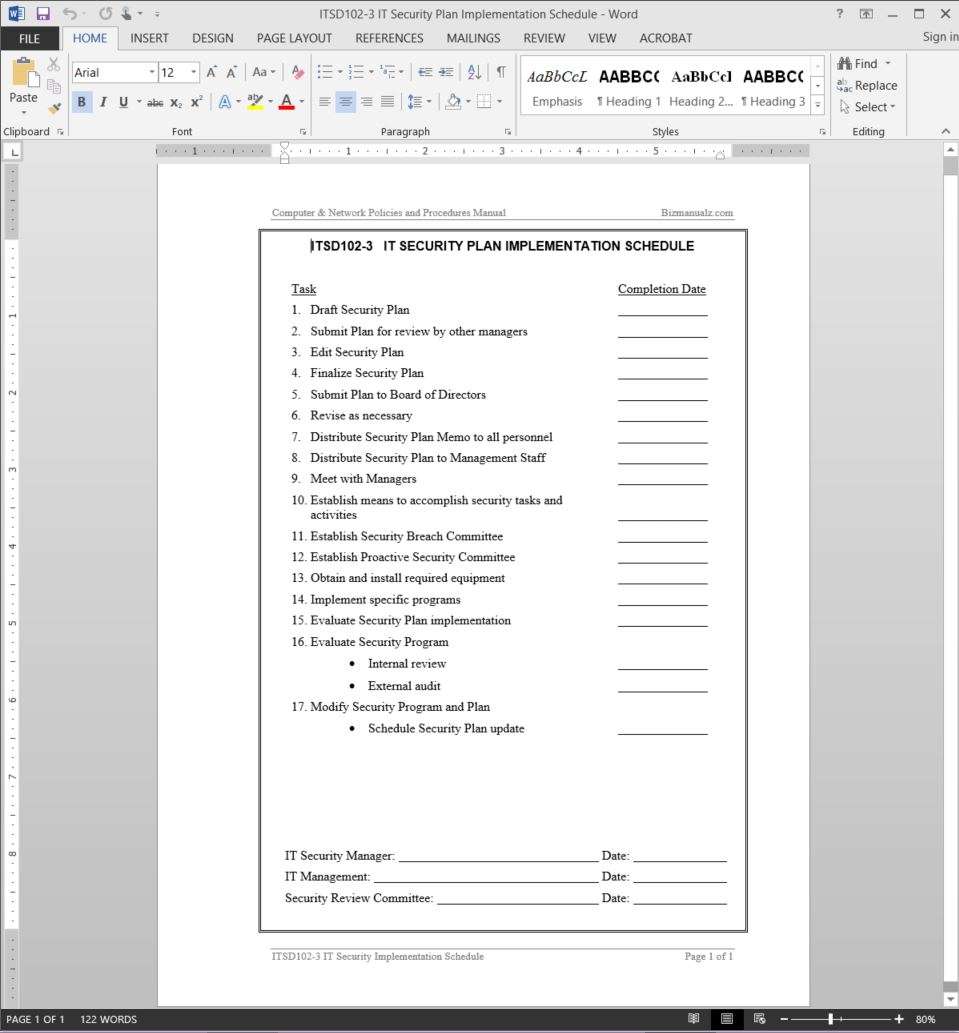
A plan to determine who is in charge and who is responsible for each action covered below. This 25 page word template and 7 excel templates including a threats matrix risk assessment controls identification and authentication controls. The following types of resources are available for use to complete the security plan. A standard is typically a collection of system specific or procedural specific requirements that must be met by everyone.
The organization develops and implements a security plan for the information system that provides an overview of the security requirements for the system and a description of the security controls in place or planned for meeting those requirements. In the event that a system is managed or owned by an external. For example you might have a standard that describes how to harden a windows 81 workstation for placement on an external dmz network. The planning for this thing starts much ahead of the system being implemented and used.
The usf it network security plan establishes guidelines for it practices used on a day to day basis to provide a secure and robust computing environment. Blank document that includes the minimum required elements.








.gif)